Sometimes, things are not as they appear to be. Recently, a WhatsApp message appeared with the text of:
*Rolex is giving away 3000 Free Set of Watches* to celebrate its 93rd anniversary. Get your free Watch at: http://www.rolẹx.com/
Looking closely at the letter “e” in Rolex I saw a small dot under the letter e. This is actually a Vietnamese letter:
https://en.wiktionary.org/wiki/%E1%BA%B9
Hiding letters and tricking users to visiting malware sites via Unicode homographs is not a new style of attack:
https://www.theguardian.com/technology/2017/apr/19/phishing-url-trick-hackers
and there is even a Wiki page describing the issue and possible solutions:
https://en.wikipedia.org/wiki/IDN_homograph_attack
When translating the text of http://www.rolẹx.com into ASCII one will get:
This domain was registered on March 29 by someone in Denver, Colorado and the website was placed on an AWS instance.
Since there is no malware code in this URL, all anti-virus engines will mark it as valid and clean. That page redirects the user to another site: http://go.oclasrv.com/afu.php?zoneid=1619146
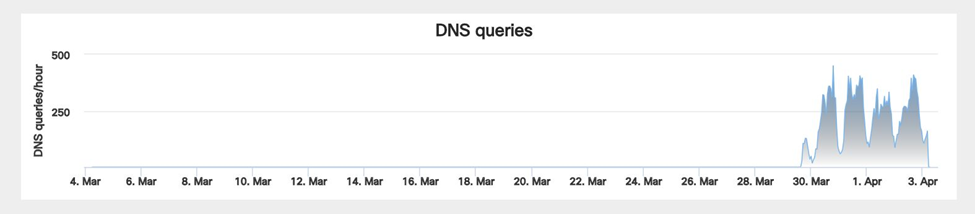
On March 30, only one malware analysis engine flagged this site as malicious.
One can easily see the start of this malware campaign via the use of Cisco’s Umbrella Investigate service:
Fortunately, the malware campaign appears to be mainly centered in the US, Pakistan, Turkey and Egypt with Israeli users only being 1.02% of those who have been lured into clicking on the fake Rolex site.
Bottom line: beware of free giveaways and always examine links very carefully.
Hank Nussbacher is Director of Network & Computing Infrastructure. He has worked at IUCC for the past 30 years and is responsible for network design, the NOC team, the CERT team and the cloud team.